 Physical Security
Physical Security ISO45001
ISO45001 Security Act
Security Act
 ISO45001
ISO45001 Security Act
Security Act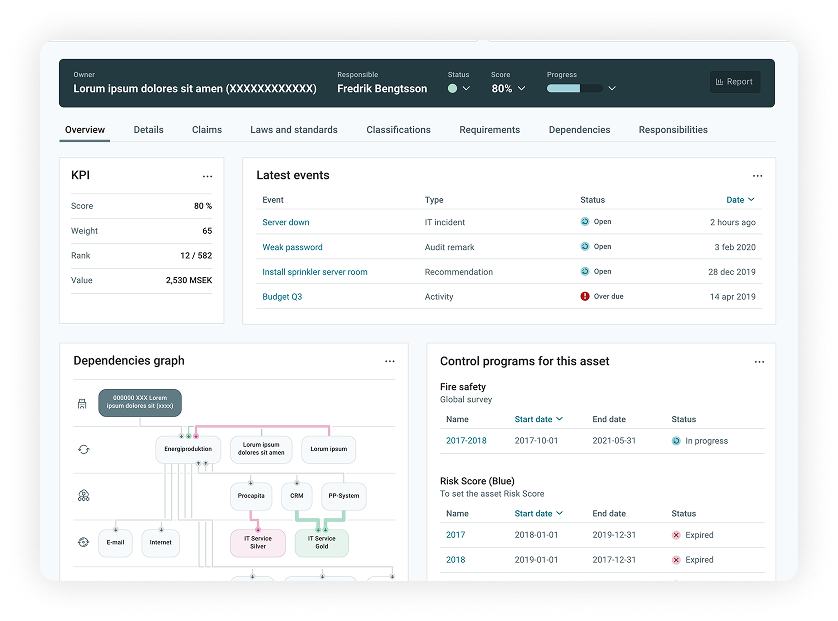
The goal of physical security is to protect facilities, buildings, areas, and objects from unauthorized access, damage, or theft. Physical security integrates with several other areas with specific requirements:
Physical security – Security Protection Act: The purpose of the Security Protection Act is to prevent security-classified information, operations, or facilities from being damaged or falling into the wrong hands. This is achieved by identifying what needs to be protected and the threats that exist. In a risk and vulnerability analysis, three main tasks are carried out: 1. Mapping assets – what needs to be protected, 2. Analyzing threat scenarios, 3. Assessing vulnerabilities. In addition to the risk and vulnerability analysis, important steps include designing physical protective measures, implementing technical systems, routines and organization, as well as follow-up and maintenance. iFACTS supports documentation and structure for these processes. For more information, see the section Security Protection.
Physical security – Crime prevention work: This involves working systematically to reduce the risk of crimes such as burglary, theft, vandalism, and robbery. Common steps include threat and risk assessments, protective measures, and cooperation. iFACTS supports documentation and structure for these processes.
Physical security – Work environment and personnel safety: Physical security is also an important part of workplace safety. It is about protecting staff from threats and violence. Common steps include personal protection, access control, and evacuation plans. For more information, see the section Work Environment.
Physical security – Protection of property and assets: A fundamental form of physical security involves protecting material assets. This may include burglary protection, insurance, and inventory control. iFACTS provides well-developed support for this. See also Loss Prevention for more information, as well as Information Security for more information.
iFACTS offers a powerful and user-friendly IT support system for organizations that need to manage and follow up on requirements related to physical security. The system is designed to ensure regulatory compliance, simplify administration, and create structure in information management where requirements for protection, traceability, and documentation are particularly high.
With iFACTS you get support for the entire chain in physical security – from mapping to follow-up. The system enables the management of:
- Security protection agreements with both internal and external parties
- Facility Assets documentation and protection class
- Security-related matters and classified information
- Incident and nonconformity management in the security area
- Contingency planning with the ability to administer war organizations, roles, human resources, vehicles and equipment in a coherent flow
- Risk, threat and vulnerability assessment integrated into the various processes
- Documentation and control of physical protection measures, such as access control systems, alarms and camera surveillance
Due to well-defined processes, controlled permissions and automated notifications, security work becomes both more efficient and more traceable.
Streamlined handling with emphasis on security and flexibility
To meet varying requirements from different types of operations, iFACTS offers several installation options. The system can be delivered as:
- On-premises installation: Run iFACTS entirely within your own IT environment, fully disconnected from external systems or cloud providers — ideal for organizations with strict sovereignty and security requirements.
- SaaS delivery: Hosted in secure Swedish datacenters within the EU/EEA. Each customer receives a dedicated instance with no shared environments.
iFACTS' hosting infrastructure is designed for high standards of information security and availability. All data transfers are encrypted, backups are performed daily and stored for a minimum of 365 days, and regular restore tests are carried out to ensure reliability. Backup and retention policies can be tailored to your specific needs.
Benefits Across the Entire Organization
By digitalizing your security workflows, iFACTS supports:
- Reduce case processing time
- Minimize manual handling
- Increased quality and traceability
- Improve control and follow-up
- Ensure secure and compliant management of sensitive data
The platform is built to support public sector organizations and critical infrastructure operations with high demands on security, transparency, and data protection.
Benefits
With iFACTS, you gain comprehensive support for physical security, covering facility data, asset classification, security measures, security protection agreements, third-party documentation, risk management, and supplier oversight. The platform enables a structured, traceable, and standards-compliant approach to physical security, seamlessly integrating with incident management, risk assessments, deviations, and dependencies.
Clear and accurate reporting to management is essential — ensuring leaders can take responsibility and be held accountable.
Workflows
- Facility documentation, security classification
- Dependencies between facilities, processes, and resources
- Security Protection Agreement (SUA in Swedish)
- Third-party control
- Personnel security, work environment
- Inspection, patrolling
- Fire protection, SBA (Systematic Fire Protection Work)
- Risk and vulnerability analysis
- Incident and deviation management
- Continuous monitoring of physical security
- Management reporting
Contact

Simon Tegnell
Phone: +46 72 562 20 15
Email: simon.tegnell@ifacts.se










