 Information Security
Information Security ISO27000
ISO27000 NIS2
NIS2 GDPR
GDPR Cyber Security Act
Cyber Security Act
 ISO27000
ISO27000 NIS2
NIS2 GDPR
GDPR Cyber Security Act
Cyber Security Act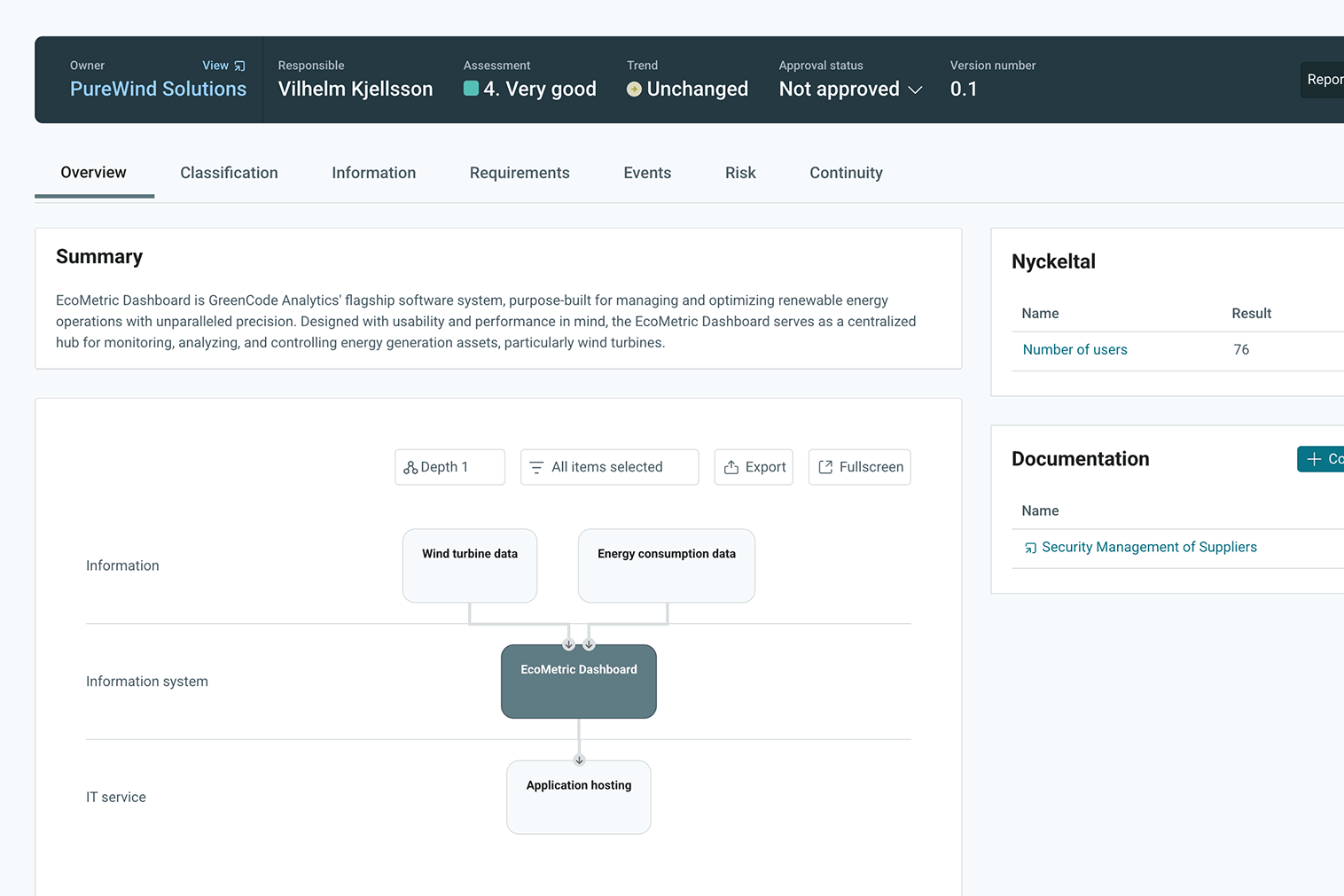
The requirements are increasing for organizations to demonstrate how they govern and lead. Specifically, they must show how they achieve goals, meet requirements, and comply with legislation regarding information security and GDPR.
Furthermore, the ongoing trend of digitalization aims to make operations more efficient, but at the same time, it opens up numerous threats and vulnerabilities. For instance, these threats include cyberattacks that can knock out entire operations, the improper handling of sensitive information, and risks to critical control systems for utilities like electricity and water supply. Modern information security management needs to be able to govern the growing digital world.
Several different types of legislation, norms and standards affect safety work:
- The NIS Directive
- The Protective Security Act
- GDPR - The General Data Protection Regulation
- The ISO 27000 series
Recently, authorities and governing bodies have updated their recommendations and requirements. The Swedish Civil Contingencies Agency (MSB) recently released a report with 20 recommendations for companies operating in modern IT landscapes.
The report also shows that changes made without oversight and without clear information security work can cause damage. The opposite is also true, when organizations fail to implement necessary changes, they risk major damage. For example, attackers can exploit known vulnerabilities in systems that the organization has not updated.
Structured work with iFACTS for better information management processes
iFACTS' method is based on process orientation and asset management – inspired by the ISO 27000 series. Common work steps within information security are: ownership, responsibility, classification, requirements management, policy, document management, dependencies, GAP analysis, deviation and risk management.
iFACTS also supports the certification process for an ISMS (Information Security Management System) in accordance with ISO 27001. From scoping, risk management, selection of controls including the Statement of Applicability, to rollout and implementation.
Practical work with Information Security
Through asset management, the organization inventories its assets and defines clear areas of responsibility. iFACTS supports information classification according to ISO 27000 but also supports other classifications according to other standards, internal governing documents, and laws in accordance with business-specific requirements. This work allows the organization to use a tailored list of requirements based on its own needs and on requirements from ISO 27000, where it can continuously monitor compliance and actively register and manage deviations.
The risk module interweaves the inventory, classification, and requirements management of assets to help you identify risks and create mitigating actions. The iFACTS system makes risk management a natural part of asset management. Control tasks are set up continuously with our check & control feature to easily measure compliance with all or parts of the ISO 27000 standard.
GDPR linked to Information Security
GDPR is handled within information security. Each processing activity is registered as an asset, and all necessary functionality is available in the iFACTS software. For example: register of processing activities, DPIA, data breach reporting, consent management, information on stored data, and erasure.
Benefits
With iFACTS you get full control over information security – from classification to incident management. The platform supports a structured, traceable and standards-based security approach where you can easily see connections between assets, risks and processes. The result? Reduced vulnerability, improved compliance and higher trust throughout the organization.
Workflows
- Documentation including classification of information and assets
- Visualization of IT resource dependencies
- Document and policy management with version control and access rules
- Requirements management based on laws, internal rules, contractual obligations
- Management of security incidents and nonconformities
- Risk and continuity management linked to the entire supply chain – systems, processes or suppliers
- Control and audit
- Management reporting
Contact

Simon Tegnell
Phone: +46 72 562 20 15
Email: simon.tegnell@ifacts.se

Mark Wijeyratne
Phone: +46 72 741 39 00
Email: mark.wijeyratne@ifacts.se
Case

Information Security & GDPR at City of Malmö
“Supports the system owners to compile requirements without being IT-specialists.”


Digitalize Information Security at Region Västernorrland
“The region estimates that it can reduce time spent on information classification with up to 80%”








